The quantity of cyber strikes and also information violations in current years is staggering as well as it's simple to generate a shopping list of companies that are house names that have been influenced. Right here are simply a few instances. For the full checklist, see our largest information breaches message. The Equifax cybercrime identity burglary event affected roughly 145.
In this circumstances, safety concerns and also solutions were additionally endangered, boosting the danger of identification burglary. The violation was initially reported by Yahoo on December 14, 2016, and also required all affected individuals to change passwords as well as to reenter any unencrypted safety questions as well as answers to make them secured in the future.
Cyber Security Company for Dummies

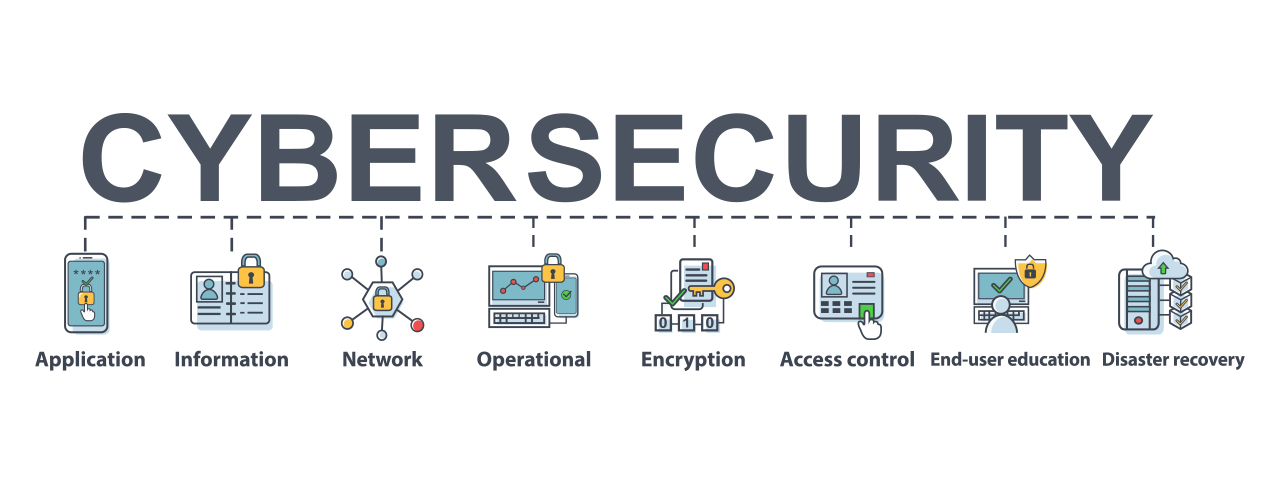
Cybersecurity is similar to a bar or a club that weaves together several procedures to protect itself and also its clients. The most common spyware typically tape-records all user task in the gadget where it is mounted. This leads to assaulters figuring out delicate information such as debt card details.

Cybersecurity is a huge umbrella that covers different security parts. It is very easy to get overloaded and lose emphasis on the large image. Right here are the top ten best methods to comply with to make cybersecurity efforts extra reliable. A cybersecurity strategy need to start with recognizing all components of the framework and also individuals that have accessibility to them.
A Biased View of Cyber Security Company
This is either done by internet services exposed by each solution or by allowing logs to be legible among them. These remedies must have the ability to expand in tandem with the company and with each other. Shedding track of the most recent safety and security patches as well as updates is very easy with several protection solutions, applications, systems, as well as gadgets entailed - Cyber Security Company.
The even more crucial the source being secured, the more find out here now frequent the upgrade cycle needs to be. Update strategies have to be component of the initial cybersecurity strategy.
Cyber Security Company Can Be Fun For Everyone
The National Cyber Security Partnership recommends a top-down approach to cybersecurity, with company monitoring leading the fee across organization procedures. By incorporating input from stakeholders at every degree, even more bases will be covered. Despite having the most advanced cybersecurity technology in place, the obligation of safety frequently drops on the end user.
An informed staff member base has a tendency to enhance security position at every level. It is apparent that despite the sector or size of an organization, cybersecurity is a developing, important, and also non-negotiable process that expands with any type of business. To guarantee that cybersecurity efforts are heading in the best direction, most countries have regulating bodies (National Cyber Security Centre for the U.K., NIST for the united state, etc), which issue cybersecurity standards.
The Cyber Security Company Diaries
We carried out a study to much better recognize how boards deal with cybersecurity. We asked directors just how usually cybersecurity was talked about by the board and found that only 68% of participants stated regularly or constantly.
When it concerns understanding the board's function, there were numerous options. While 50% of respondents said there had been conversation of the board's function, there was no consensus concerning what that role should be. Giving advice to running supervisors or C-level leaders was viewed as the board's duty by 41% of participants, getting involved in a tabletop exercise (TTX) was discussed by 14% of the participants, and also general awareness or "on call to react needs to the board be needed" was stated by 23% of Directors.
Cyber Security Company Things To Know Before You Get This
There are lots of frameworks readily available to help a company with their cybersecurity strategy. It is easy and also offers executives and directors a great framework for assuming via the crucial facets of cybersecurity. important link It likewise has numerous degrees of detail that cyber professionals can utilize to install controls, processes, as well as procedures.
The 9-Minute Rule for Cyber Security Company